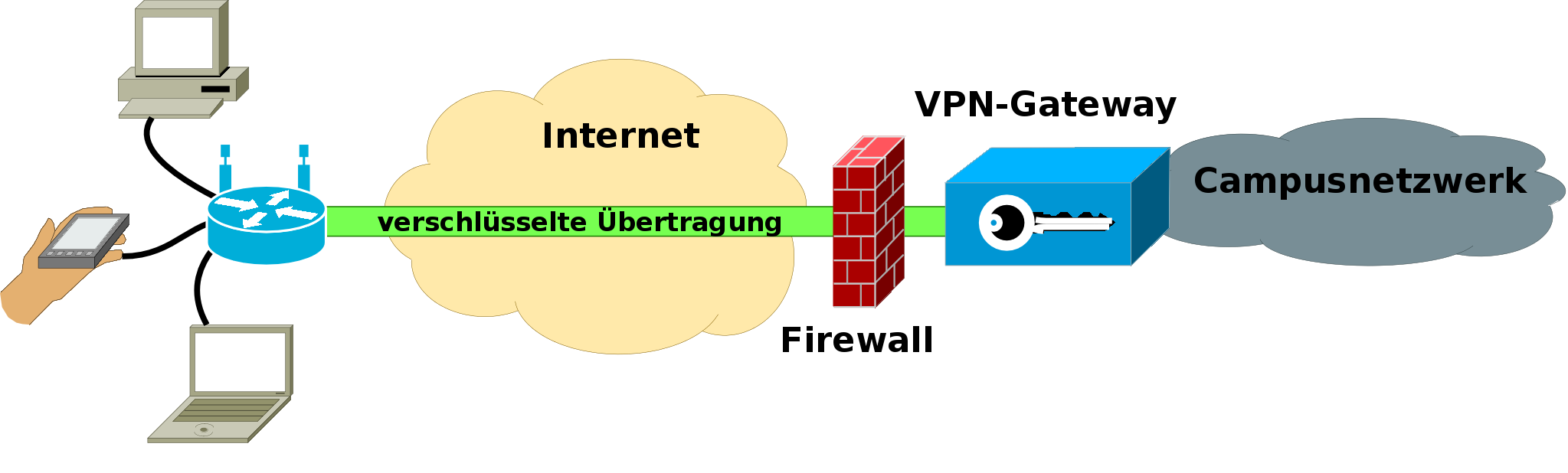
If you are in a public network, for example at university or the airport, your traffic can be recorded and decrypted. To prevent others from doing that you can send your traffic through a secured VPN-tunnel. The VPN-tunnel leads your traffic encrypted to a server which is processing your requests.
In the following tutorial you will learn how to run OpenVPN Server on your Raspberry Pi:
Raspbian or a similar distribution.
Step 1
To be able to install the latest programversions we should update our packet sources:
sudo apt-get update
Step 2
Now we are installing OpenVPN and OpenSSL.
sudo apt-get install openvpn openssl
Step 3
We are switching to the directory of OpenVPN and paste a directory we will be needing later into it.
cd /etc/openvpn
sudo cp -r /usr/share/doc/openvpn/examples/easy-rsa/2.0 ./easy-rsa
Step 4
Now we open the file easy-rsa/vars with nano and apply some changes.
nano /easy-rsa/vars
export EASY_RSA="`pwd`"
export EASY_RSA="/etc/openvpn/easy-rsa"
Step 5
We change the directory, log in as root user and execute some configurations.
cd easy-rsa
sudo su
source vars
./clean-all
./pkitool --initca
ln -s openssl-1.0.0.cnf openssl.cnf
Step 6
Now we are able to generate the components for the encryption of OpenVPN. After the first input you will be asked for the abbreviation of your country (US = USA, DE – Germany, AT = Austria, CH – Switzerland). All other inputs can simply be confirmed.
./build-ca OpenVPN
./build-key-server server
./build-key client1
Step 7
The calculation of the last components can take a few minutes.
./build-dh
exit
Step 8
We have to switch the directory again and create the file openvpn.conf with the following content:
cd ..
sudo touch openvpn.conf
sudo nano openvpn.conf
dev tun
proto udp
port 1194
ca /etc/openvpn/easy-rsa/keys/ca.crt
cert /etc/openvpn/easy-rsa/keys/server.crt
key /etc/openvpn/easy-rsa/keys/server.key
dh /etc/openvpn/easy-rsa/keys/dh1024.pem
user nobody
group nogroup
server 10.8.0.0 255.255.255.0
persist-key
persist-tun
status /var/log/openvpn-status.log
verb 3
client-to-client
push "redirect-gateway def1"
#set the dns servers
push "dhcp-option DNS 8.8.8.8"
push "dhcp-option DNS 8.8.4.4"
log-append /var/log/openvpn
comp-lzo
You can change the DNS-servers to any DNS you like.
Step 9
Now, create the internet-forwarding for the CPN clients. If you are not using an ethernet-cable (e.g. Wifi) you will have to replace “eth0″ with the name of your network device.
sudo sh -c ‘echo 1 > /proc/sys/net/ipv4/ip_forward’
sudo iptables -t nat -A POSTROUTING -s 10.0.0.0/8 ! -d 10.0.0.0/8 -o eth0 -j MASQUERADE
Step 10
One of the final steps will be to delete the “#” before net.ipv4.ip_forward=1 in sysctl.conf.
cd ..
sudo nano sysctl.conf
Step 11
A part of the above settings have to be endorsed as a crontab to work permanently. Insert following line at the end of the crontab file (replace “eth0″ if you did above):
crontab -e
@reboot sudo iptables -t nat -A POSTROUTING -s 10.0.0.0/8 ! -d 10.0.0.0/8 -o eth0 -j MASQUERADE
Step 12
Again change to the root-user and to the directory /etc/openvpn/easy-rsa/keys in which we will create the file raspberrypi.ovpn and fill it with the code of the second paragraph. RASPBERRY-PI-IP should be replaced by the IP address of your Pi or, if you are using a DynDNS service, by the given domain.
sudo su
cd /etc/openvpn/easy-rsa/keys
nano raspberrypi.ovpn
dev tun
client
proto udp
remote RASPBERRY-PI-IP 1194
resolv-retry infinite
nobind
persist-key
persist-tun
ca ca.crt
cert client1.crt
key client1.key
comp-lzo
verb 3
Step 13
Now create a packet with all the needed files for the client, which we will place in /home/pi and give the user pi the needed rights to the file.
tar czf openvpn-keys.tgz ca.crt ca.key client1.crt client1.csr client1.key raspberrypi.ovpn
mv openvpn-keys.tgz /home/pi
chown pi:pi /home/pi/openvpn-keys.tgz
exit
Step 14
Restart the OpenVPN server.
sudo /etc/init.d/openvpn start
Finished! Now we are able to download the file die openvpn-keys.tar.gz on the client and extract the files to your OpenVPN client folder.
An OpenVPN Client for Windows is: http://openvpn.se/
for Mac: https://code.google.com/p/tunnelblick/
Linux users simply install the packet openvpn







Hi,
Thx for your blog, it triggered my project.
All went well so far. However, client says
“No server certificate verification method has been enabled”
Any idea?
Thx & greetz from Germany,
Volker
Hi Volker,
this is only a security issue and irrelevant for your connection.
http://forum.openvpn.eu/viewtopic.php?f=1&t=461 Kurze Erklärung auf deutsch
Greetz
Rezin
Excellent idea. I just got my Raspberry Pi. Biggest problem….I keep finding reasons to buy more Pis. This is yet another one.
Yes, if I find a project that needs a constant use of my RasPi I immediately want to buy at least two new ones
Firstly, thank you for this wonderful tutorial. I don’t want to turn this into a help forum but I’m wondering if I’m the only one having an issue with access the internet through the raspberry pi? I am able to connect to my devices on the remote site but internet access times out. I believe it has to do with the iptables that were supposed to be created using sudo iptables -t nat -A POSTROUTING -s 10.0.0.0/8 ! -d 10.0.0.0/8 -o eth0 -j MASQUERADE
I ran iptables -L and it appears no rules have been applied. See output below: -
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Any help with this would be much appreciated.
Just restarted the Raspberry PI and now I have internet access across the VPN. I ran itables -L again but got the same output as above? Would be nice to know if I was troubleshooting the right area? Anyways, all up and working! Fantastic day
I’m glad you have internet access, I do not really know if there is something wrong with your IP tables

If you have further questions I’d advise you to look into the OpenVPN help forums, great people there